Weeks ago, we released a trailer of our work in progress collaboration tool for VTubers — Playground.
Soon we found ourselves getting into a lot of controversy about the security of the platform and the technology behind it. In this article, I am going to address them one by one.
Through this, I hope to shed light on a brighter future for VTuber collab tools and be transparent to the community.
After reading most of the tweets about related concerns, we have synthesized them into three major categories of Live2D model security concerns.
1. Room intercept by uninvited person?
2. The invited person might easily get the model data?
3. Platform risk?
And following the early feedback from the community, we have taken the time to look into the matters, here’s what has progressed to mitigate the issues.
| Room intercept by uninvited person
1. The room id is generated randomly each time with UUID v4, with the password option, you can add further protection to your room to prevent uninvited access.
| The invited person might easily get the model data
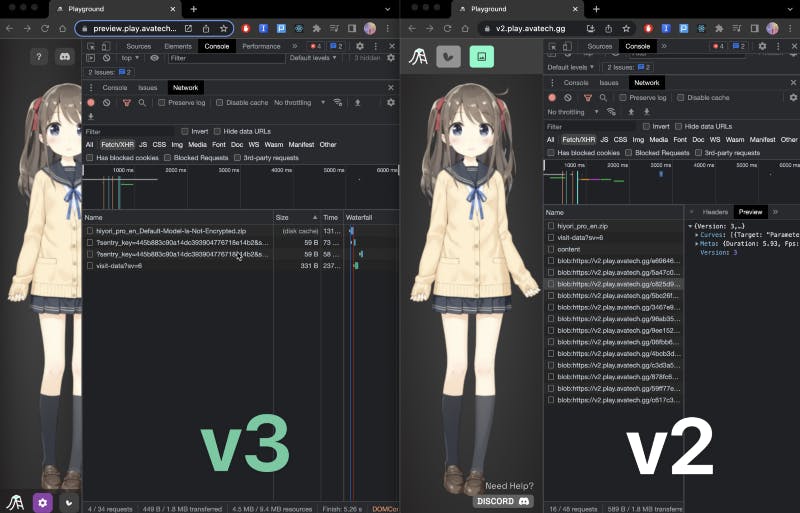
2. Since Playground is built on web technology, by going into the developer tools panel, the network details will be visible to the end-user. Similar to how VRoid Hub was doing to prevent the texture from showing up in the dev tools (OBUCHI Yutaka’s Presentation), by decoding the texture ourselves and loading them as array bufferdata directly to the rendering layer in memory (pixijs & Cubism SDK for Web), we were able to hide the model-related data (JSON, moc3, png) from network request.
| Platform risk
3. Valid concerns were raised about model security towards the platform, we have since then adopted E2EE (End to End Encryption) to ensure only the client in the room will be able to decrypt your model. Therefore, the actual model data in transit and in the cache will stay safe from third parties.
To give you a high-level overview of how we handle the model files, here is a simplified graph outlining the model life cycle.
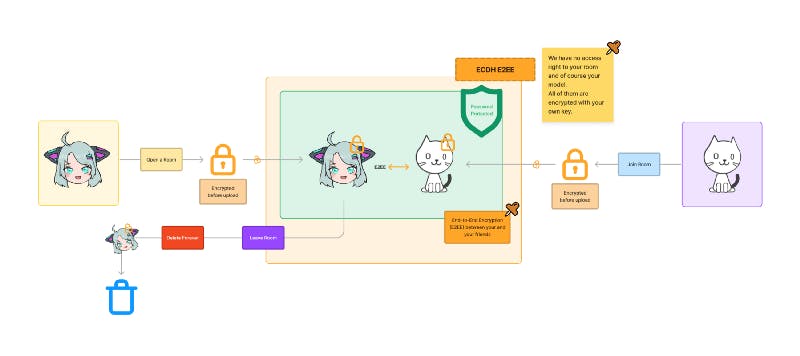
We have implemented ECDH (Elliptic-curve Diffie–Hellman) for end-to-end encryption. Under the hood, each time you join a room, a public and private key (ECDH) will be created, and a symmetric key (AES-GCM) is generated and used to encrypt the actual model file once before transfer. When each user joins the same room, they will request the asymmetric key from your client, and then the key will be sent end-to-end encrypted via ECDH protocol.
Throughout the transmission process, the Playground server will not gain access to your private key and will not be able to decrypt your model. The model files will be cleared from our server once you left the room since it is only used to relay to other members in the room.
For more details about the Playground V3 and other improvements, the changelog is here https://docs.avatech.ai/change-log.
At Avatech we are building an accessible platform for all kinds of avatars to connect with each other. We are committed to bringing a safe environment to your collab experience.
I would like to thank everyone who helped the community by raising these concerns publicly, via Twitter DM, and various Discord servers.
Please do let us know if you were able to find any further security issues in Playground (DM us in discord), and if you wanna try out Playground Beta, reach out to us in Discord (https://avatech.gg/discord).
See you next time!
Benny
Avatech
